With more devices, the demand for Linux knowledge will continue to grow. At the same time, the demand for security is higher than ever. All the media attention and regulations like GDPR, asks for more Linux security specialists. The Red Hat Customer Portal delivers the knowledge, expertise, and guidance available through your Red Hat subscription. The Linux system has its own security configuration and management system to address the security requirements in an enterprise environment.
We can choose which actions on. It works on the kernel level, where it can. This is the default log file for the Linux audit daemon. The file has a capture of all related audit events. It has been configured in auditd.
Usually there is no reason to alter this location, unless a different. Linux systems are popular in many organizations, and auditing the syslogs of the Linux systems can provide important information on the events in your network. This information will help you decide on various administrative and security actions. How can I use audit to see who changed a file in Linux? Modern Linux kernel (.x) comes with auditd daemon.
Auditing Linux systems involves: Auditing Linux. A variety of methods exist for auditing user activity in UNIX and Linux environments. Some of them come preinstalled within common distributions, some can be downloaded as freeware, and some are commercially available products.
In our last article, we have explained how to audit RHEL or CentOS system using auditd utility. The audit system (auditd) is a comprehensive logging system and doesn’t use syslog for that matter. It also comes with a tool-set for managing the kernel audit system as well as searching and producing. Lynis is a battle-tested security tool for systems running Linux , macOS, or Unix-based operating system.
It performs an extensive health scan of your systems to support system hardening and compliance testing. For a deep penetrating scan of your Linux servers and desktops, turn to the Lynis auditing tool. Check out how to install and use Lynis. Every system on your business network needs auditing at. FIPS Validated Cryptographic Modules for Oracle Linux 7. The latest development release is 3. Enabling FIPS Mode on Oracle Linux 7. Welcome the Linux Audit Documentation Project.
The Linux Audit Documentation project is intended to hold documentation and specifications related to the Linux Audit project. We have a page describing the process for reporting and bugs and requesting features. Reporting Bugs and Feature Requests. Kali Linux , with its BackTrack lineage, has a vibrant and active community. With active Kali forums, IRC Channel, Kali Tools listings, an open bug tracker system and community provided tool suggestions – there are many ways for you to get involved in Kali Linux today.
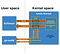
Recommended Linux security audit checklist guide Audit Policy settings for PCI DSS and other compliance standards – configuration settings for audit. Use of the linux audit policy to generate audit logs is an essential best practice for compliance and security. Its vital to get expert advice, not just to make sure you are getting all. Installing and Using the OpenSSL FIPS Object Module 7.
No comments:
Post a Comment
Note: only a member of this blog may post a comment.